Palo Alto VPN download unlocks a world of secure online access. Imagine seamlessly connecting to your work network from anywhere, safeguarding your sensitive data with robust encryption. This comprehensive guide walks you through the process, from understanding the basics of VPNs to configuring your Palo Alto VPN connection.
This guide covers everything from the fundamental principles of virtual private networks (VPNs) to the specifics of installing and configuring the Palo Alto VPN client. We’ll also delve into security best practices and troubleshooting common issues. Get ready to navigate the digital landscape with confidence and peace of mind.
Configuration and Setup
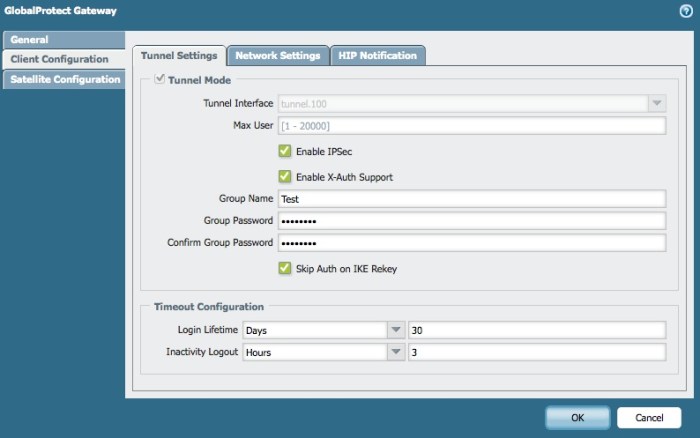
Navigating the world of VPNs can feel like venturing into a new frontier. Palo Alto Networks VPNs, however, offer a remarkably user-friendly experience, particularly when you grasp the essentials of configuration. This section provides a practical guide to setting up your Palo Alto VPN, covering everything from initial setup to managing various connection types.Setting up a Palo Alto VPN is not rocket science, but understanding the required parameters is key to a seamless connection.
Knowing how to configure essential settings and input accurate network information ensures a stable and reliable connection. We’ll break down the process step-by-step, allowing you to confidently configure your VPN, whether for remote access or site-to-site communication.
Typical Configuration Process
The Palo Alto VPN configuration process is designed to be intuitive and straightforward. The initial steps typically involve logging into the Palo Alto Networks device’s management interface. From there, you’ll navigate to the VPN configuration section, where you’ll specify the desired connection type and configure relevant settings. This usually includes specifying the remote network’s details and authenticating users.
Essential Settings and Parameters
Several key settings are critical during setup. These include, but aren’t limited to, the VPN type (e.g., site-to-site, remote access), encryption protocols (e.g., IPsec, OpenVPN), authentication methods (e.g., username/password, certificates), and pre-shared keys (for site-to-site configurations). Precisely configuring these parameters ensures secure and efficient communication. Careful attention to these details is paramount.
Network Information Requirements, Palo alto vpn download
To establish a connection, you need accurate network information. This typically includes the IP address or domain name of the remote network, gateway addresses, subnet masks, and DNS server information. Ensure the accuracy of this data, as any discrepancies can hinder the connection process. A meticulous approach is vital.
Connection Types
Understanding the different connection types is crucial. Site-to-site VPNs connect two or more networks, enabling seamless communication between them. Remote access VPNs allow users to securely connect to a network from remote locations. Choosing the right connection type is critical to your specific networking needs.
Establishing a VPN Connection
After configuring the essential settings and providing the necessary network information, the actual process of establishing a VPN connection typically involves clicking a ‘Connect’ button or initiating a similar action within the interface. This initiates the connection process, which may involve authentication and verification steps. Success hinges on the accuracy of prior configuration steps.
Configuration Steps Summary
| Step | Action | Description |
|---|---|---|
| 1 | Log in to the Palo Alto Networks device management interface. | Access the administrative panel to manage VPN configurations. |
| 2 | Navigate to the VPN configuration section. | Locate and access the specific settings for establishing VPN connections. |
| 3 | Specify the VPN type (e.g., site-to-site, remote access). | Select the appropriate connection type based on your network requirements. |
| 4 | Configure encryption protocols, authentication methods, and other settings. | Define security parameters for a secure connection. |
| 5 | Provide the necessary network information. | Input accurate details of the remote network to establish a connection. |
| 6 | Initiate the VPN connection. | Start the connection process by clicking the ‘Connect’ button or similar action. |
Security Considerations

Protecting your sensitive data and ensuring a secure connection is paramount when utilizing a VPN like Palo Alto. This section Artikels crucial security best practices to keep your virtual tunnel safe and your data protected. A robust security strategy is essential to safeguard your digital assets in today’s interconnected world.A strong VPN solution, like Palo Alto, acts as a shield, encrypting your online traffic and masking your IP address.
However, even the most sophisticated VPN requires proactive measures from the user to maximize its effectiveness. Understanding potential vulnerabilities and implementing preventative measures is key to ensuring a secure and reliable virtual connection.
Strong Passwords and Authentication
A robust password policy is the cornerstone of any secure system. Complex passwords, incorporating a mix of uppercase and lowercase letters, numbers, and symbols, are vital for thwarting unauthorized access attempts. Using a password manager can significantly enhance password security, and two-factor authentication (2FA) adds an extra layer of protection. Regularly changing passwords, especially after any security breach, is another critical security measure.
Protecting Against VPN Vulnerabilities
Maintaining vigilance against vulnerabilities is crucial for any VPN user. Staying updated with the latest security patches and firmware updates for your VPN client is essential. Regularly scanning your system for malware and employing robust antivirus software are additional preventative measures. Avoid using public Wi-Fi networks for sensitive transactions while connected to a VPN. This crucial step helps to mitigate the risks associated with potentially compromised public networks.
Potential Risks and Threats
VPN usage, while offering increased security, isn’t without potential risks. Malware, phishing attempts, and malicious actors attempting to exploit vulnerabilities in the VPN infrastructure are potential threats. Compromised VPN servers or weak authentication protocols can lead to data breaches. Understanding these potential threats is the first step in mitigating their impact.
Troubleshooting Common Security Issues
Encountering security issues with your Palo Alto VPN is a possibility. If your VPN connection drops frequently, investigate network congestion or firewall conflicts. If you suspect a security breach, immediately disconnect from the VPN, change your password, and report the incident. Checking for conflicting software or incompatible applications can help pinpoint the source of the problem.
Enhancing Security Measures
To elevate security beyond basic protocols, consider employing advanced features offered by Palo Alto VPN. Implementing strict access controls, logging activities, and regularly auditing your system for unauthorized access attempts are crucial. Regular security audits can help identify potential vulnerabilities and enhance overall system security. Employing encryption protocols like OpenVPN or WireGuard adds an extra layer of protection to your VPN connection.
Troubleshooting Palo Alto VPN Connections: Palo Alto Vpn Download
Navigating the digital frontier can sometimes feel like a thrilling expedition, but like any journey, there are occasional bumps in the road. This section will equip you with the tools to identify and resolve common issues you might encounter while connecting to your Palo Alto VPN. We’ll explore the most frequent problems, and provide actionable steps to get you back online smoothly.Troubleshooting VPN connectivity is a crucial skill, akin to understanding the mechanics of your favorite vehicle.
A solid grasp of these techniques ensures a seamless and secure online experience, regardless of the challenges you may face.
Common Connection Issues
Understanding the common stumbling blocks is the first step towards a smooth connection. Below are the most frequent issues users encounter when attempting to connect to a Palo Alto VPN. A well-prepared traveler anticipates potential roadblocks and is ready with contingency plans.
- Connection Timeouts: Often, connection timeouts stem from network instability or server overload. This can manifest as a slow response or a complete failure to establish a connection. Network congestion or firewall restrictions are common culprits. Consider checking your internet connection, or temporarily disabling any security software to rule out interference.
- Authentication Failures: Incorrect login credentials are the most frequent reason for authentication failures. Ensure the username and password are entered accurately. Double-check capitalization, special characters, and any password policies in place. If you suspect a compromised account, immediately change your password.
- Configuration Errors: Incorrect VPN settings can lead to connection problems. Verify that the VPN server address, username, and other relevant settings are configured correctly according to your organization’s guidelines. A thorough review of the configuration settings is essential.
- DNS Resolution Issues: DNS resolution errors prevent the VPN client from locating the server. Verify that your DNS settings are correctly configured on your local network. Temporarily using a known-working DNS server can help identify the source of the problem.
Resolving Connection Timeouts
Connection timeouts can be frustrating, but often stem from readily fixable issues. Addressing these problems can be as simple as checking your internet connection.
- Verify Internet Connectivity: Ensure your internet connection is stable and working correctly. Try other online services to rule out broader internet problems.
- Check Network Interference: Temporarily disable any firewalls or security software that might interfere with the VPN connection. Interference from other network devices can also impact performance.
- Restart Router/Modem: A simple reboot can resolve transient network issues. A restart often clears temporary glitches in your network infrastructure.
- Contact Network Support: If the issue persists, consult your network administrator or IT support team. They can provide further assistance, especially if the problem stems from broader network infrastructure.
Troubleshooting Authentication Failures
A common roadblock is incorrect credentials, but other factors can contribute.
- Verify Credentials: Double-check your username and password for accuracy. Typos or incorrect capitalization can lead to authentication failures. Review the authentication requirements of your VPN service.
- Password Complexity: Ensure your password adheres to the complexity requirements set by your organization. Strong passwords are your first line of defense against unauthorized access.
- Network Connectivity: Confirm that your network connection is stable and not experiencing any outages. Interruptions in connectivity can prevent successful authentication.
- Account Status: Check your account status to ensure your account is active and not suspended or locked.
Addressing Configuration Errors
Incorrect configurations are frequent causes of VPN connection issues. A careful review of the settings can resolve the problem.
- Review Configuration: Carefully review your VPN client configuration settings, ensuring all required fields are filled correctly. Refer to your organization’s VPN configuration guide for the precise details.
- Verify Server Address: Double-check the VPN server address to ensure it’s accurate. Typographical errors can cause the connection to fail.
- Contact Support: If you suspect a configuration error, contact your organization’s support team for assistance. They can provide guidance specific to your configuration.
Alternative VPN Solutions
Exploring the digital landscape reveals a wealth of VPN options beyond the familiar Palo Alto VPN. Understanding these alternatives allows for informed decisions, catering to diverse needs and preferences. Each option brings its own set of advantages and disadvantages, demanding a nuanced perspective.
Exploring the Market
The VPN market is vibrant, offering a plethora of choices. From user-friendly interfaces to advanced security features, each vendor strives to capture a slice of the market. Several notable alternatives stand out, each with unique strengths and weaknesses.
Key Alternative VPN Providers
Several VPN providers compete with Palo Alto VPN, offering varied features and price points. A crucial element in selecting the right VPN is understanding the specific requirements for your use case. Evaluating the pros and cons of each solution helps in making a more informed choice.
Comparison Table
| Feature | Palo Alto VPN | ExpressVPN | NordVPN |
|---|---|---|---|
| Security | Robust, enterprise-grade encryption | Military-grade encryption, strong security protocols | Advanced encryption, multiple security protocols |
| Speed | Generally fast, but performance may vary based on server location | Known for consistently high speeds and global server network | Fast connections, extensive server network globally |
| Ease of Use | Complex configuration for advanced users; relatively simple for basic usage | User-friendly interface, intuitive setup process | Intuitive interface, straightforward setup |
| Pricing | Typically part of a larger security suite, pricing varies with features | Competitive pricing across different subscription plans | Competitive pricing with various subscription plans |
| Features | Advanced features like granular access control, VPN concentrators | Extensive server network, specialized features like split tunneling | Large server network, features like dedicated IP addresses |
ExpressVPN: Speed and Global Reach
ExpressVPN boasts a vast global network of servers, contributing to consistent speed and reliability. Its user-friendly interface makes it accessible to users of varying technical proficiency. The emphasis on speed makes it an attractive choice for users prioritizing fast streaming and seamless online experiences.
NordVPN: Security and Features
NordVPN stands out for its robust security features and extensive list of add-ons. From double VPN encryption to dedicated IP addresses, NordVPN caters to a wide range of user needs. Its comprehensive feature set and reputation for security make it a solid contender.
